Machine Learning And Hardware Security Challenges And Opportunities
However the implications of hardware security problems under a massive diffusion of machine learning techniques are still to be completely understood. Organizations and people are growing increasingly dependent on digital infrastructure for a range of processes from payments to communication platforms.

Cato Networks Introduces A New Ai System To Eliminate False Positives In Security Systems Artificialintelligence Mac Security System Deep Learning Networking
Security is another issue related to machine learning.

Machine learning and hardware security challenges and opportunities. It is also advantageous because such edge devices are capable of filtering data reducing noise and improving data quality on the spot. They helped improving our everyday routines but they also demonstrated to be an extremely helpful tool for more advanced and complex applications. However the implications of hardware security problems under a massive diffusion of machine learning techniques are still to be completely understood.
But while this sounds quite promising for the advocates of machine learning in cybersecurity. Key challenges and data sets. IoT Machine Learning Is Human-Centered Machine Learning.
Some of the prominent barriers to designing high performance and energy-efficient multi-core microprocessors and SoCs in the sub-10nm technology nodes will be outlined. The program was rich engaging and filled with current themes and research outcomes spanning theory and practice in Machine Learning. Machine learning techniques have significantly changed our lives.
For some applications the goal is to analyze and understand the data to identify trends eg surveillance portablewearable electronics. Timely detection of the security threat or dangerous malware is the key to gain a competitive and proactive lead in providing security safeguards. Hardware Trojans are malicious hardware inclusions that leak secret information degrade the performance of the system or cause denial-of-service.
It is not surprising that most of the security analysts are challenged by the vast amount of raw data from dialing monitoring systems even though there are several tools to help them analyze and interpret this. Hardware for Machine Learning. The challenges and opportunities for machine learning in the IoT June 4.
We now use ML-based systems to optimize business processes improve productivity and enhance product quality. Challenges and Opportunities Invited Paper Vivienne Sze Yu-Hsin Chen Joel Emer Amr Suleiman Zhengdong Zhang Massachusetts Institute of Technology Cambridge MA 02139 AbstractMachine learning plays a critical role in extracting meaningful information out of the zetabytes of sensor data collected every day. This four-day virtual conference brought together academics researchers and PhD Students.
Machine learning plays a critical role in extracting meaningful information out of the zetabytes of sensor data collected every day. 12222016 by Vivienne Sze et al. For some applications the goal is to analyze and understand the data to identify trends eg surveillance portablewearable electronics.
Machine learning for cybersecurity. For some applications the goal is to analyze and understand the data to identify trends eg surveillance portablewearable electronics. In other applications the goal is to take.
Hardware for Machine Learning. Machine learning plays a critical role in extracting meaningful information out of the zetabytes of sensor data collected every day. New paradigm shifts necessary for integrating special-purpose machine learning accelerators and hardware security processors into next-generation SoCs will be explored.
Challenges and opportunities for sub-7nm process machine learning and hardware security technologies in the rapidly evolving IoT industry. Hardware for Machine Learning. Challenges and Opportunities for Sub-5nm Machine Learning Accelerators and Hardware Security Technologies Dr.
For machine learning technology to play a big role in cybersecurity the biggest challenge on the path is to detect and potential security threats or malware. The risk of Hardware Trojans is increasing due to the outsourcing of the VLSI manufacturing process to different entities and the incorporation of third. In other applications the goal is to take immediate action based the data eg roboticsdrones self-driving.
For some applications the goal is to analyze and understand the data to identify trends eg surveillance portablewearable electronics. In other applications the goal is to take immediate action. With Moores law process technology scaling well into the nano-scale regime future SoC platforms ranging from high performance cloud.
Pre-silicon Security Signoff from C to GDSII Mark Tehranipoor University of Florida. Machine learning plays a critical role in extracting meaningful information out of the zetabytes of sensor data collected every day. This paper first highlights novel applications of machine learning for hardware security such as evaluation of post quantum cryptography hardware and extraction of physically unclonable functions from neural networks.
Preliminaries Hardware Security Problems Addressed by Machine Learning Algorithms. Machine Learning in Cyber Security When we look at the recent landscape in the cyber security industry the collection and storage of large amounts of useful data points is already in place. Ram Kumar Krishnamurthy Senior Research Director and Senior Principal Engineer Intel Labs USA CAD for SoC Security.
0 share Machine learning plays a critical role in extracting meaningful information out of the zetabytes of sensor data collected every day. This approach is particularly attractive when enhanced security is desired. Hardware for machine learning.
The first virtual Frontiers in Machine Learning event took place from July 20-23 2020.

5 Snowflake Benefits For Your Business Data Warehouse Snowflakes Data

Understanding Iot Security Part 1 Of 3 Iot Security Architecture On The Device And Communication Layers Security Architecture Cyber Security Iot
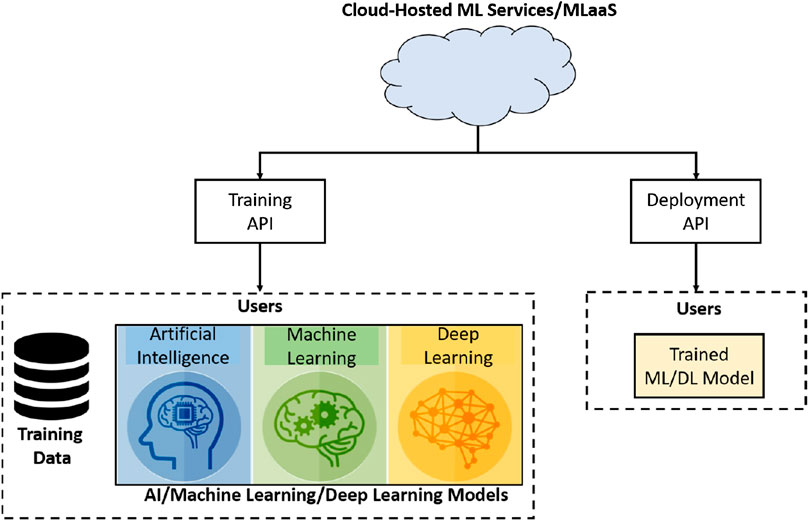
Frontiers Securing Machine Learning In The Cloud A Systematic Review Of Cloud Machine Learning Security Big Data

In The Present Scenario When Everything Is Going Online And The Amount Of Data That Is Generated Online Is M Cyber Security Machine Learning Computer Security

Hardware Security A Hands On Learning Approach Paperback Walmart Com In 2021 Nanotechnology Hands On Learning Learning

A Security Guard Protects An Eleven Year Old Girl Who Is Being Targeted By A Gang For Participating As A Trial Witne Iot Online Safety Metal Detectors For Kids
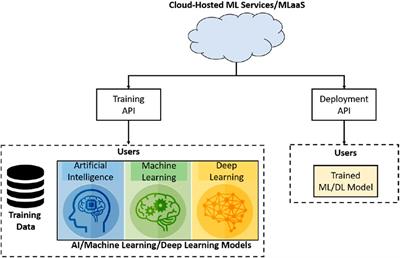
Frontiers Securing Machine Learning In The Cloud A Systematic Review Of Cloud Machine Learning Security Big Data

Securing The Deep Learning Stack Nervana Deep Learning Data Science Learning

Figure 3 From Designing Serious Games For Cyber Ranges A Socio Technical Approach Semantic Scholar Cyber Security Education Thinking Skills Systems Thinking

Table 3 From Applications In Security And Evasions In Machine Learning A Survey Semantic Scholar Machine Learning Learn Computer Science Learning Techniques

Security Challenges For The Future Of The Internet Arduino Top Software Simple Arduino Projects

Cyber Security Training Courses Security Training Cybersecurity Training Cyber Security Course

How To Become A Cyber Security Engineer Cyber Security How To Become Engineering

4 Multi Perspective Modeling And Holistic Simulation Complexity Challenges In Cyber Physical Systems Cyber Physical System Complex Systems Systems Thinking

Pros And Cons Of Cyber Security Jobs Cyber Security Course Cyber Security Cyber Security Career

Infographic Cybersecurity Databreaches Ransomware Atp Cybersecurity Cybercrime Cyberc Cybersecurity Infographic Cyber Security Cyber Security Awareness

Figure 7 From The Design And Implementation Of Language Learning Chatbot With Xai Using Ontology And Tran Learning Techniques Chatbot Computational Linguistics

Advantages Of Machine Learning Machine Learning Security Solutions Data Science

Hardware Acceleration Of Recurrent Neural Networks The Need And The Challenges Computer Architecture Networking Challenges
Post a Comment for "Machine Learning And Hardware Security Challenges And Opportunities"